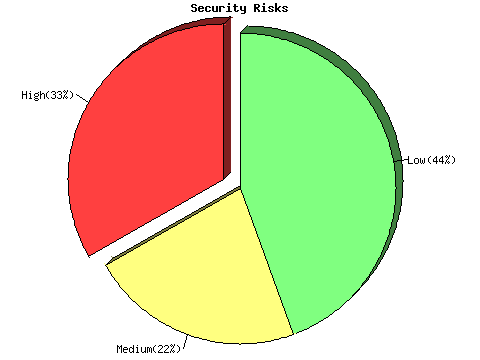

Vulnerability found on port netbios-ssn (139/tcp)
Vulnerability found on port netbios-ssn (139/tcp)
Vulnerability found on port netbios-ssn (139/tcp)
Warning found on port netbios-ssn (139/tcp)
Here is the browse list of the remote host :
PC01 - celeron
PC02 - celeron
PC03 - celeron
PC04 - celeron
This is potentially dangerous as this may help the attack
of a potential hacker by giving him extra targets to check for
Solution : filter incoming traffic to this port
Risk factor : Low
Nessus ID : 10397
Warning found on port netbios-ssn (139/tcp)
Here is the list of the SMB shares of this host :
ADMIN$ -
IPC$ - Vzd len komunikace proces
This is potentially dangerous as this may help the attack
of a potential hacker.
Solution : filter incoming traffic to this port
Risk factor : Medium
Nessus ID : 10395
Warning found on port netbios-ns (137/udp)
. The following 8 NetBIOS names have been gathered :
PC01 = This is the computer name registered for workstation services by a WINS client.
UCEBNA = Workgroup / Domain name
PC01 = Computer name that is registered for the messenger service on a computer that is a WINS client.
PC01
UCEBNA = Workgroup / Domain name (part of the Browser elections)
STUDENT01 = Computer name that is registered for the messenger service on a computer that is a WINS client.
UCEBNA
__MSBROWSE__
. The remote host has the following MAC address on its adapter :
0x00 0xc0 0xa8 0xf4 0xcb 0x99
If you do not want to allow everyone to find the NetBios name
of your computer, you should filter incoming traffic to this port.
Risk factor : Medium
CVE : CAN-1999-0621
Nessus ID : 10150
Vulnerability found on port general/tcp
Warning found on port general/tcp
The remote host uses non-random IP IDs, that is, it is
possible to predict the next value of the ip_id field of
the ip packets sent by this host.
An attacker may use this feature to determine if the remote
host sent a packet in reply to another request. This may be
used for portscanning and other things.
Solution : Contact your vendor for a patch
Risk factor : Low
Nessus ID : 10201
Information found on port general/tcp
Remote OS guess : Windows NT4 or 95/98/98SE
CVE : CAN-1999-0454
Nessus ID : 11268
Warning found on port general/icmp
The remote host answers to an ICMP timestamp
request. This allows an attacker to know the
date which is set on your machine.
This may help him to defeat all your
time based authentication protocols.
Solution : filter out the ICMP timestamp
requests (13), and the outgoing ICMP
timestamp replies (14).
Risk factor : Low
CVE : CAN-1999-0524
Nessus ID : 10114
Warning found on port general/icmp
The remote host answered to an ICMP_MASKREQ
query and sent us its netmask (255.255.255.0)
An attacker can use this information to
understand how your network is set up
and how the routing is done. This may
help him to bypass your filters.
Solution : reconfigure the remote host so
that it does not answer to those requests.
Set up filters that deny ICMP packets of
type 17.
Risk factor : Low
CVE : CAN-1999-0524
Nessus ID : 10113
Information found on port general/udp
For your information, here is the traceroute to 10.0.0.21 :
10.0.0.21
Nessus ID : 10287